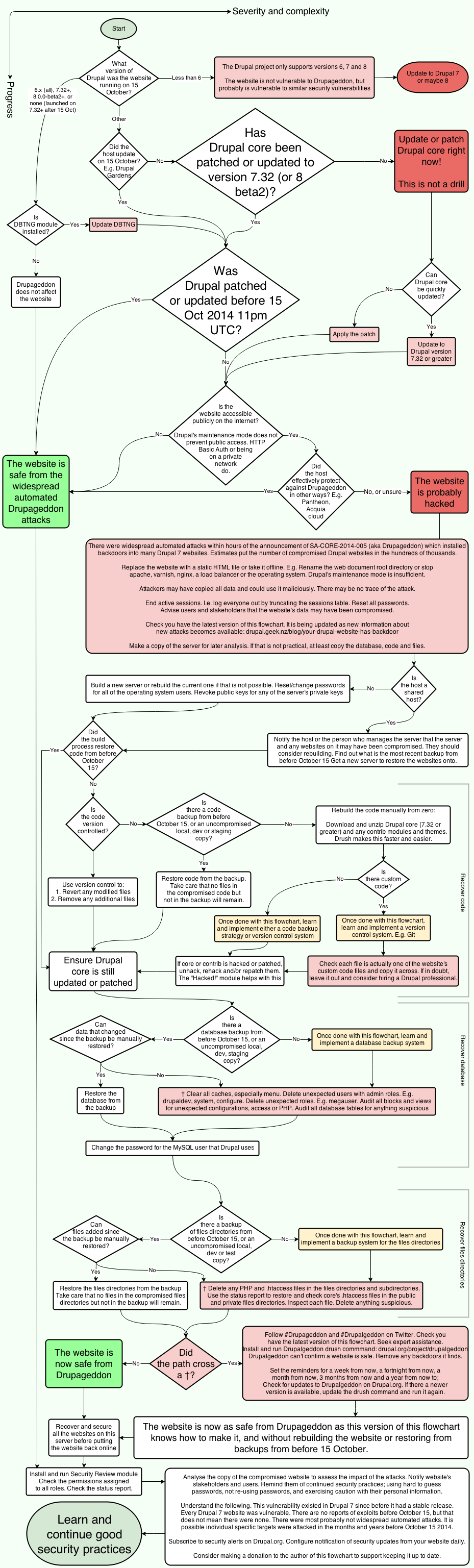
Your Drupal website has a backdoor
I estimate hundreds of thousands of Drupal websites now have backdoors; between ten and ninety percent of all Drupal websites. Automated Drupageddon exploits were in the wild within hours of the announcement. Updating or patching Drupal does not fix backdoors that attackers installed before updating or patching Drupal. Backdoors give attackers admin access and allow arbitrary PHP execution.
If your Drupal 7 (and 8) website is not updated or patched it is most likely compromised. If your website was not updated within a day of the announcement, it is probably compromised. Even if your website was updated within a day, it may be compromised.
If you did not know, Drupageddon is the highly critical SQL injection vulnerability in Drupal core announced 15 October. It is also known as Drupalgeddon (with an "L"), CVE-2014-3704, Drupal SA core 2014 005 and #DrupalSA05. Drupageddon (no "L") is the original name selected by Stefan Horst, who initially reported to the Drupal security team. See Drupageddon.com.
I have drafted this flowchart to help Drupal website administrators understand their options for recovering from Drupageddon. Review, feedback and collaboration is welcome.
The flowchart is a living document. Currently version is number 7.
Updates
- The Drupal security team has published PSA-2014-003, a public service announcement about recovering websites compromised by Drupageddon exploits. The official recommendation is: Restore from pre-October-15-backups. This is good advice. (I co-authored the PSA.)
- Also read Greg Knaddison's "Your Drupal site got hacked. Now what?"
- Please do not share by copying the image or image link. Instead share the link to this blog post. That way anyone who needs it can be sure to using the most up to date version of it.
- This flowchart is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.